 Challenger and Flamory
Challenger and Flamory
Flamory provides the following integration abilities:
- Create and use window snapshots for Challenger
- Take and edit Challenger screenshots
- Automatically copy selected text from Challenger and save it to Flamory history
To automate your day-to-day Challenger tasks, use the Nekton automation platform. Describe your workflow in plain language, and get it automated using AI.
Screenshot editing
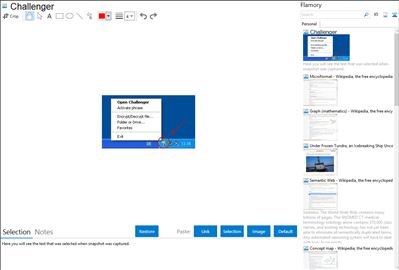
Flamory helps you capture and store screenshots from Challenger by pressing a single hotkey. It will be saved to a history, so you can continue doing your tasks without interruptions. Later, you can edit the screenshot: crop, resize, add labels and highlights. After that, you can paste the screenshot into any other document or e-mail message.
Here is how Challenger snapshot can look like. Get Flamory and try this on your computer.
Application info
Challenger is a software for the encoding of files, folders and drives. For the installation and for the execution simple user rights suffice. Thereby the program is mobil usable on an USB flash drive too. The software is conceived for the local protection of data privacy and for closed communication circles. A synchronous stream cipher, a development from Germany, delivers a fast encryption.
The program use a two key procedure. One of the keys represents a conventional memory phrase or password. The second key is created by an extensive list (3 MB) with real random numbers. It is generated individually also and can be handled like a material key (safe). The second key can be formed independent of the PC platform for high security requirements also. Attacks with keylogger remain ineffective because to spy out the passport phrases for a deciphering of your data does not suffice.
Mobile encoding, USB flash drive software
If the program is copied on an USB flash drive, you can use Challenger on every computer. For the execution simple user rights suffice. The USB flash drive can be carried at the bunch of keys access safe. Besides the possibility encrypting data on the hard disk, you can also realize a USB flash drive encoding. So the data remain protected, if the data carrier is lost.
High security application
Challenger can be integrated into a start capable mini-Windows CD in connection with Bart's PE-Builder. You work with a write-protected system. Thereby the key generator is safe from possible operating system offsets or Trojan Horses.
Further characteristics
A safe reference check recognize manipulations at the program
Corrupt cryptic grams are recognized
Original data are deleted for certain ( the safest method: German procedure, VSITR )
The phrase concept guarantees simple and sure dealing with the program
Integration level may vary depending on the application version and other factors. Make sure that user are using recent version of Challenger. Please contact us if you have different integration experience.